Curve Block Oracle
Curve’s Roman Agureev presents a modular, open-source framework for secure multichain messaging—built with storage proofs, bridge-agnostic transport, and already live across 20+ networks. It’s now available to any team building cross-chain infrastructure.
Why Multichain Messaging Is Still Tough
Curve’s core contracts and DAO live on Ethereum, yet the protocol is deployed on 20+ networks. Each chain wants governance messages, oracle prices, and config changes in real time, but bridges remain inconsistent and occasionally dangerous. Native bridges (e.g. with Optimism and Arbitrum) are low-risk but chain-specific; generic layers (LayerZero, CCIP) cover many networks but add protocol risk. Protocols that are deployed on multiple networks want to minimize the work put into the bridging solutions they use, but also don’t want a single point of failure that could drain TVL or freeze the protocol.
To address this, Curve has developed an open-source solution that offers a modular, fault-tolerant alternative - using storage proofs and minimal trust in the transport layer.
Storage Proofs: The Minimal-Trust Backbone
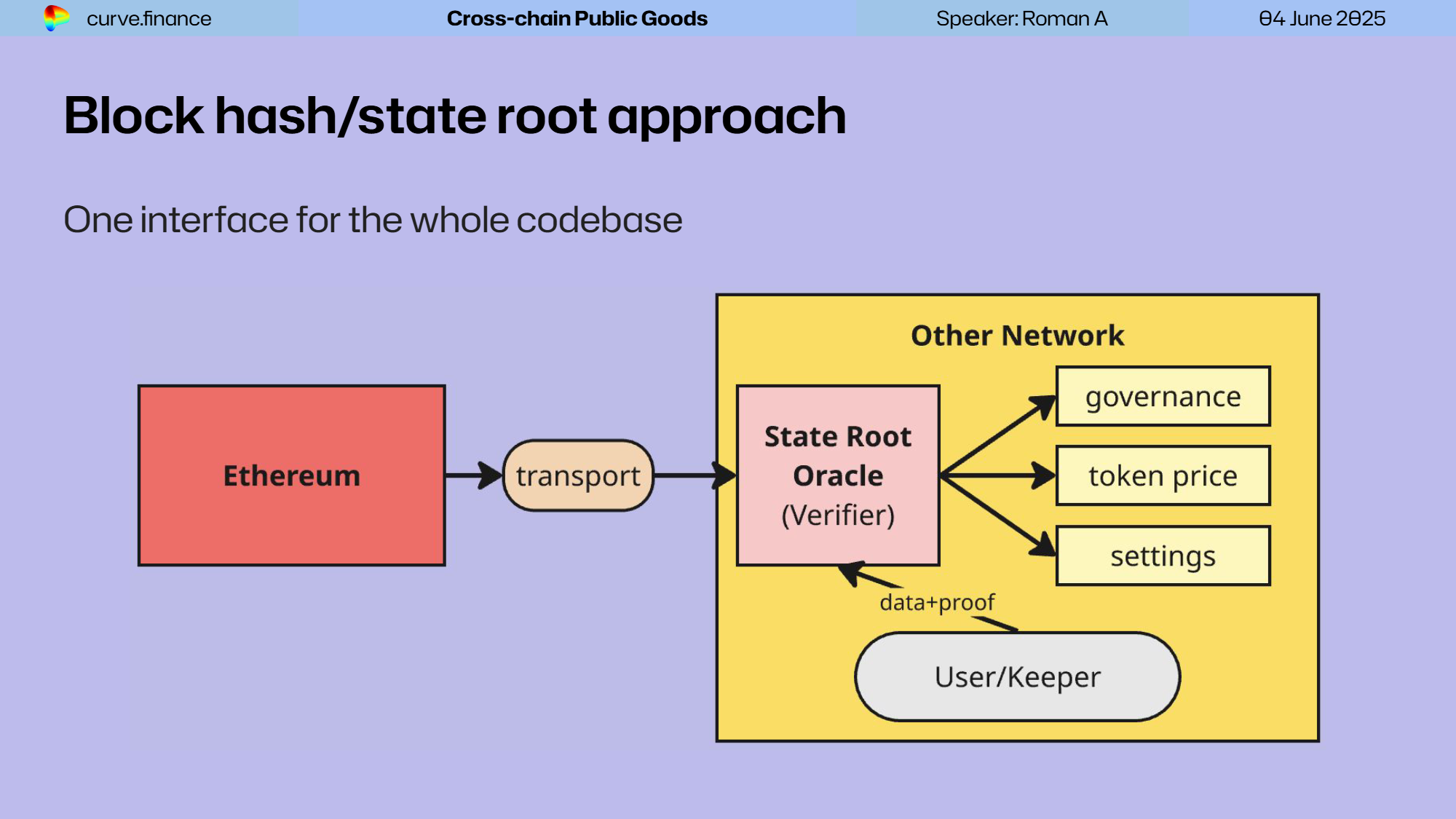
The core process for verifying data is straightforward. Curve’s system minimizes trust by relying on a basic but robust flow:
- Transport only the blockhash using a native bridge or LayerZero.
- Keepers/users submit Merkle-Patricia-Trie storage proofs on the destination chain to retrieve the exact storage slot.
- Apps consume the verified data (governance actions, crvUSD price, etc.) with no dependency on a single bridge.
Curve Block Oracle: Design Choices
The Curve Block Oracle system is designed to be lightweight, modular, and easy to integrate. Below are key architectural choices that shape its design and functionality:
- Bridge strategy:
- Native bridge where available (cheapest, zero extra trust)
- LayerZero today for L1s and fresh Curve DEX deployments
- Support for more bridging protocols like Axelar and CCIP possible through third-party DVN like CrossCurve
- Language choice: Vyper, to stay consistent with Curve contracts. As Vyper lacked support for dynamic arrays at the time, the storage-proof verifier was ported from a large Solidity library and rewritten in Vyper to ensure auditability.
Using the Curve Block Oracle
The Curve Block Oracle is designed to be simple to adopt. Whether you're building a governance module, oracle-dependent app, or a full DeFi system across chains, the integration flow is lightweight and transport-agnostic:
- Get the verifier code – The core repos are blockhash-oracle (for blockhash transport) and storage-proofs (for verifying state). The storage-proofs repo has been audited through a public Cyfrin CodeHawks contest; a formal ChainSecurity audit for the blockhash-oracle will be linked once finalized.
- Choose a transport layer – Use a native bridge where possible for lowest trust assumptions. Where a native bridge isn’t available or supported, LayerZero is the default fallback.
- Send the blockhash, verify the proof – Submit the blockhash via your transport layer and the Merkle-Patricia-Trie storage proof to retrieve state from Ethereum.
- Optionally reuse Curve’s Oracle stack – For protocols already interacting with Curve, you can consume verified state updates (like crvUSD price) with no added trust assumptions.
What’s Next
The verifier is live across Curve’s existing multichain deployments and will continue rolling out with new Curve DEX integrations. We welcome other teams to adopt or build on the system. The audit by ChainSecurity will be linked when available.
Vulnerability Disclosure
While porting a widely used Solidity Merkle proof verification library to Vyper, we discovered a critical vulnerability: it failed to properly check that each node in the proof path was present, allowing false zero values to pass as valid.
The bug affected protocols such as Aave, Frax, and StakeDAO. We worked with ChainSecurity to coordinate a responsible disclosure and ensure the issue was patched across the ecosystem.
For more detail, see Roman Agureev’s technical write-up and ChainSecurity’s postmortem.
Resources
- Repos:
- Presentation slides:
- Audits:
- Storage Proofs – Cyfrin CodeHawks contest results
- Blockhash Oracle – audit link will be added once available
- Questions? Ping Roman or Michael K on Telegram, or open a GitHub issue.